s
Question
Next Gen University main campus is located in Santa Cruz. The University has recently established various remote campuses offering e-learning services. The University is using Ipsec VPN connectivity between its main and remote campuses San Jose(SJ), Los Angeles(LA), Sacremento(SAC). As a recent addition to the IT/Networking team, you have been tasked to document the Ipsec VPN configurations to the remote campuses using the Cisco Router and SDM utility. Using the SDM output from VPN Tasks under the Configure tab to answer this question.
Note:
Before reading the answers and explanations, you can try answering these 4 questions. Below are the screenshots that are necessary to answer all the questions.
Click on the Configure tab on the top menu and then click on the VPN tab on the left-side menu to see these tabs
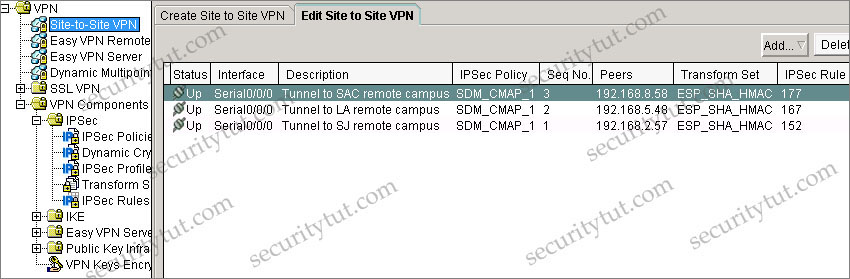
+ Tab VPN\Site-to-Site VPN (notice: you have to click on the “Edit Site to Site VPN” tab to see the image below
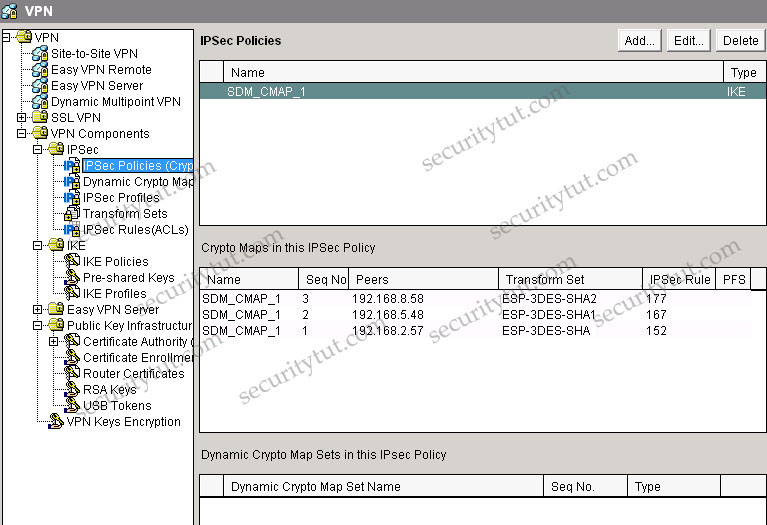
+ Tab VPN\VPN Components\IPSec\IPSec Policies
+ Tab Dynamic Crypto is empty so there is no screenshot for this tab
+ Tab IPSec Profiles is empty so there is no screenshot for this tab
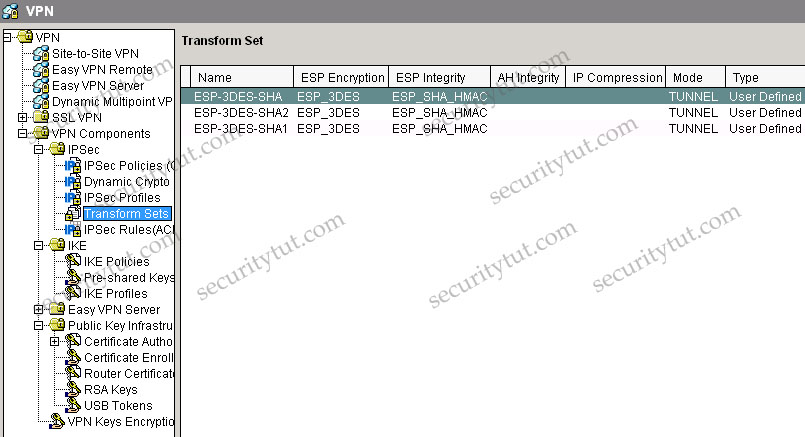
+ Tab VPN\VPN Components\IPSec\Transform Sets
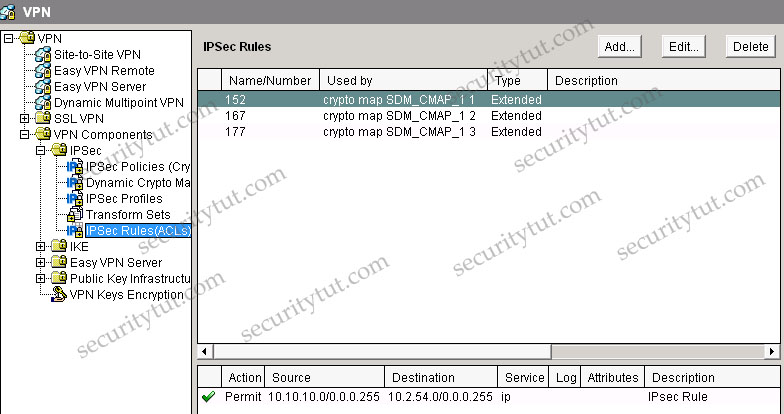
+ Tab VPN\VPN Components\IPSec\IPSec Rules
Question 1
Which one of these statements is correct in regards to Next Gen University Ipsec tunnel between its Santa Cruz main campus and its SJ remote campus?
A. It is using Ipsec tunnel mode, AES encryption, and SHA HMAC integrity Check.
B. It is using Ipsec transport mode, 3DES encryption, and SHA HMAC integrity Check.
C. It is using Ipsec tunnel mode to protect the traffic between the 10.10.10.0/24 and the 10.2.54.0/24 subnet.
D. It is using digital certificate to authenticate between the Ipsec peers and DH group 2.
E. It is using pre-shared key to authenticate between the Ipsec peers and DH group 5.
B. It is using Ipsec transport mode, 3DES encryption, and SHA HMAC integrity Check.
C. It is using Ipsec tunnel mode to protect the traffic between the 10.10.10.0/24 and the 10.2.54.0/24 subnet.
D. It is using digital certificate to authenticate between the Ipsec peers and DH group 2.
E. It is using pre-shared key to authenticate between the Ipsec peers and DH group 5.
Answer: C
Explanation
From the Site-to-site VPN tab, we specify that the SJ’s IP address is 192.168.2.57 with IPsec Rule of 152. Click on the IPSec Rules group to see what rule 152 is -> rule 152 is permit source 10.10.10.0/24 to destination 10.2.54.0/24.
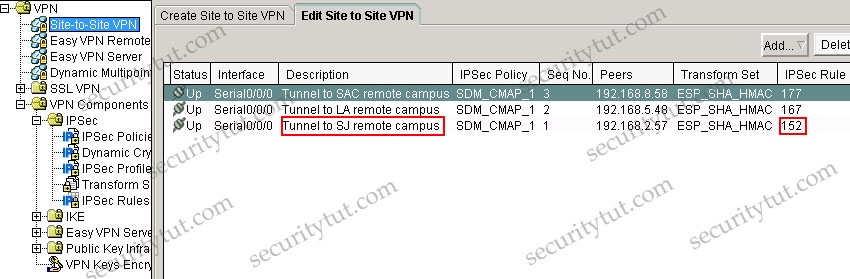
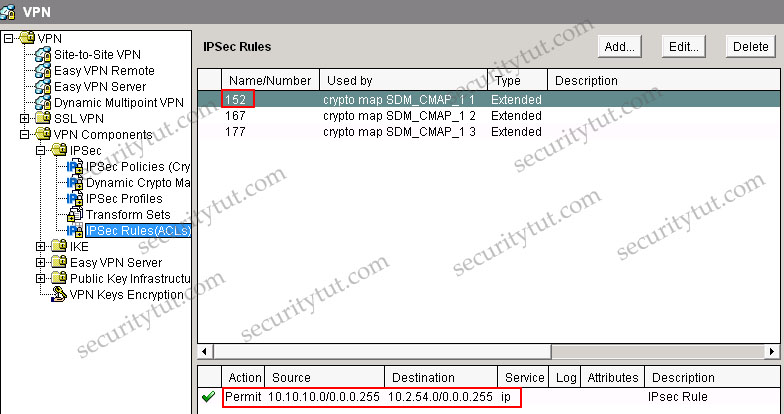
Also, in the description of the above tab, we can see “Tunnel to SJ remote campus” -> it uses Tunnel mode (although it is only the description and can be anything but we can believe it uses Tunnel mode). If you don’t want to accept this explanation then have a look at the IPSec Policy & Seq No. columns, which are SDM_CMAP_1 & 1. Click on the VPN Components\IPSec\IPSec Policies group we will learn the corresponding Transform Set is ESP-3DES-SHA. Then click on the Transform Sets group we can see the corresponding mode is TUNNEL.
Question 2
Which one of these statements is correct in regards to Next Gen University Ipsec tunnel between its Santa Cruz main campus and its SAC remote campus?
A. The SAC remote campus remote router is using dynamic IP address; therefore, the Santa Cruz router is using a dynamic crypto map.
B. Dead Peer Detection (DPD) is used to monitor the Ipsec tunnel, so if there is no traffic traversing between the two sites, the Ipsec tunnel will disconnect.
C. Tunnel mode is used; therefore, a GRE tunnel interface will be configured.
D. Only the ESP protocol is being used; AH is not being used.
B. Dead Peer Detection (DPD) is used to monitor the Ipsec tunnel, so if there is no traffic traversing between the two sites, the Ipsec tunnel will disconnect.
C. Tunnel mode is used; therefore, a GRE tunnel interface will be configured.
D. Only the ESP protocol is being used; AH is not being used.
Answer: D
Explanation
A is not correct because the VPN Components\IPSec\Dynamic Crypto Map group is empty -> the Santa Cruz router is not using a dynamic crypto map.
Not sure about answer B. We can find DPD information in the VPN Components\IKE\IKE Profiles group but I am not sure if this group exists in the exam.
C is not correct as we can use Tunnel mode without a GRE tunnel.
D is correct as we can see there is no AH configured under AH Integrity column in the VPN Components\IPSec\Transform Sets group (while in the ESP Integrity column it is ESP_SHA_HMAC).
Question 3
Which of these is used to define which traffic will be protected by IPsec between the Next Gen University Santa Cruz main campus and its SAC remote campus?
A. ACL 177
B. ACL 167
C. ACL 152
D. ESP-3DES-SHA1 transform set
E. ESP-3DES-SHA2 transform set
F. IKE Phase 1
B. ACL 167
C. ACL 152
D. ESP-3DES-SHA1 transform set
E. ESP-3DES-SHA2 transform set
F. IKE Phase 1
Answer: A
Explanation
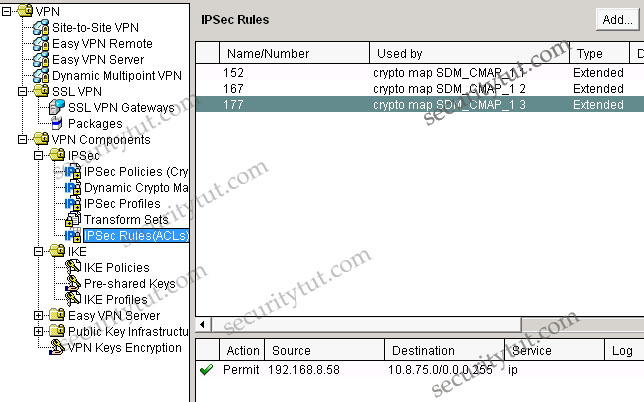
In the VPN\Site-to-site-VPN group we can easily see the SAC remote campus is protected by IPSec rule 177, which is an access-list

Question 4
The Ipsec tunnel to the SAC remote campus terminates at which IP address, and what is the protected subnet behind the SAC remote campus router? (Choose two)
A. 192.168.2.57
B. 192.168.5.48
C. 192.168.8.58
D. 10.2.54.0/24
E. 10.5.66.0/24
F. 10.8.75.0/24
B. 192.168.5.48
C. 192.168.8.58
D. 10.2.54.0/24
E. 10.5.66.0/24
F. 10.8.75.0/24
Answer: C F
Explanation
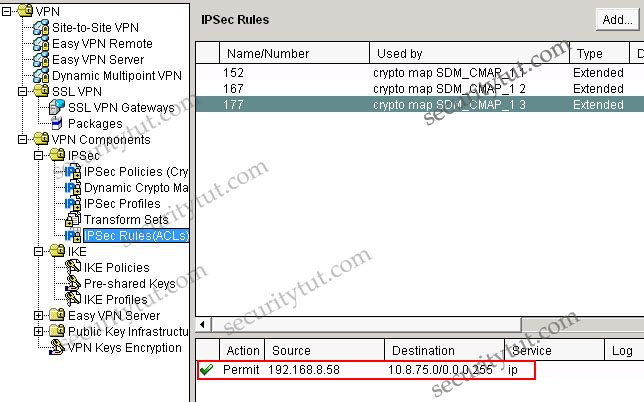
Note:
Some terminologies you should know when configuring SDM
IPSec
A framework of open standards that provides data confidentiality, data integrity, and data authentication between participating peers. IPSec provides these security services at the IP layer. IPSec uses IKE to handle negotiation of protocols and algorithms based on local policy and to generate the encryption and authentication keys to be used by IPSec. IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security gateways, or between a security gateway and a host.
IPSec Policy
In SDM, an IPSec policy is a named set of crypto map associated with a VPN connection.
Internet Key Exchange (IKE)
Internet Key Exchange (IKE) is a standard method for arranging for secure, authenticated communications. IKE establishes session keys (and associated cryptographic and networking configuration) between two hosts across the network.
Cisco SDM lets you create IKE policies that will protect the identities of peers during authentication. Cisco SDM also lets you create pre-shared keys that peers exchange.
IKE Policies
IKE negotiations must be protected; therefore, each IKE negotiation begins by each peer agreeing on a common (shared) IKE policy. This policy states which security parameters will be used to protect subsequent IKE negotiations. This window shows the IKE policies configured on the router, and allows you to add, edit, or remove an IKE policy from the router’s configuration. If no IKE policies have been configured on the router, this window shows the default IKE policy.
After the two peers agree on a policy, the security parameters of the policy are identified by a security association established at each peer. These security associations apply to all subsequent IKE traffic during the negotiation.
Hash
The authentication algorithm for negotiation. There are two possible values:
+ Secure Hash Algorithm (SHA)
+ Message Digest 5 (MD5)
+ Secure Hash Algorithm (SHA)
+ Message Digest 5 (MD5)
Authentication
The authentication method to be used.
+ Pre-SHARE: Authentication will be performed using pre-shared keys.
+ RSA_SIG: Authentication will be performed using digital signatures.
+ Pre-SHARE: Authentication will be performed using pre-shared keys.
+ RSA_SIG: Authentication will be performed using digital signatures.
D-H Group
Diffie-Hellman (D-H) Group. Diffie-Hellman is a public-key cryptography protocol that allows two routers to establish a shared secret over an unsecure communications channel. The options are as follows:
+ group1 – 768-bit D-H Group. D-H Group 1.
+ group2 – 1024-bit D-H Group. D-H Group 2. This group provides more security than group 1, but requires more processing time.
+ group5 – 1536-bit D-H Group. D-H Group 5. This group provides more security than group 2, but requires more processing time.
+ group1 – 768-bit D-H Group. D-H Group 1.
+ group2 – 1024-bit D-H Group. D-H Group 2. This group provides more security than group 1, but requires more processing time.
+ group5 – 1536-bit D-H Group. D-H Group 5. This group provides more security than group 2, but requires more processing time.
AH
Authentication Header. This is an older IPSec protocol that is less important in most networks than ESP. AH provides authentication services but does not provide encryption services. It is provided to ensure compatibility with IPSec peers that do not support ESP, which provides both authentication and encryption.
AH-MD5-HMAC: Authentication Header with the MD5 (HMAC variant) hash algorithm.
AH-SHA-HMAC: Authentication Header with the SHA (HMAC variant) hash algorithm.
AH-SHA-HMAC: Authentication Header with the SHA (HMAC variant) hash algorithm.
DES
Data Encryption Standard. Standard cryptographic algorithm developed and standardized by the U.S. National Institute of Standards and Technology (NIST). Uses a secret 56-bit encryption key. The DES algorithm is included in many encryption standards.
3DES
Triple DES. An encryption algorithm that uses three 56-bit DES encryption keys (effectively 168 bits) in quick succession. An alternative 3DES version uses just two 56-bit DES keys, but uses one of them twice, resulting effectively in a 112-bit key length. Legal for use only in the United States.
ESP
Encapsulating Security Payload. An IPSec protocol that provides both data integrity and confidentiality. Also known as Encapsulating Security Payload, ESP provides confidentiality, data origin authentication, replay-detection, connectionless integrity, partial sequence integrity, and limited traffic flow confidentiality.
+ ESP-MD5-HMAC: ESP (Encapsulating Security Payload) transform using the MD5-variant SHA authentication algorithm.
+ ESP-SHA-HMAC: ESP (Encapsulating Security Payload) transform using the HMAC-variant SHA authentication algorithm.
+ ESP-SHA-HMAC: ESP (Encapsulating Security Payload) transform using the HMAC-variant SHA authentication algorithm.
GRE
Generic routing encapsulation. Tunneling protocol developed by Cisco that can encapsulate a wide variety of protocol packet types inside IP tunnels, creating a virtual point-to-point link to Cisco routers at remote points over an IP internetwork. By connecting multiprotocol subnetworks in a single-protocol backbone environment, IP tunneling using GRE allows network expansion across a single-protocol backbone environment.
HMAC
Hash-based Message Authentication Code. HMAC is a mechanism for message authentication using cryptographic hash functions. HMAC can be used with any iterative cryptographic hash function, e.g., MD5, SHA-1, in combination with a secret shared key. The cryptographic strength of HMAC depends on the properties of the underlying hash function.
MD5
Message Digest 5. A one-way hashing function that produces a 128-bit hash. Both MD5 and Secure Hashing Algorithm (SHA) are variations on MD4 and are designed to strengthen the security of the MD4 hashing algorithm. Cisco uses hashes for authentication within the IPSec framework. MD5 verifies the integrity and authenticates the origin of a communication.
SHA
Some encryption systems use the Secure Hashing Algorithm to generate digital signatures, as an alternative to MD5.
ISAKMP
The Internet Security Association Key Management Protocol is the basis for IKE. ISAKMP authenticates communicating peers, creates and manages security associations, and defines key generation techniques.
Pre-shared Key
One of three authentication methods offered in IPSec, with the other two methods being RSA encrypted nonces, and RSA signatures. Pre-shared keys allow for one or more clients to use individual shared secrets to authenticate encrypted tunnels to a gateway using IKE. Pre-shared keys are commonly used in small networks of up to 10 clients. With pre-shared keys, there is no need to involve a CA for security.
Digital certification and wildcard pre-shared keys (which allow for one or more clients to use a shared secret to authenticate encrypted tunnels to a gateway) are alternatives to pre-shared keys. Both digital certification and wildcard pre-shared keys are more scalable than pre-shared keys.
Post a Comment